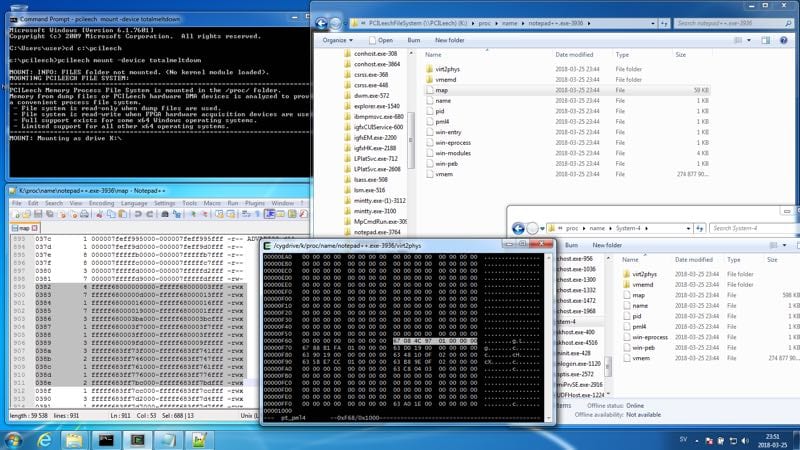
The brands have been releasing the fix for the flaws, but, now it has been discovered that with these updates Windows 7 ended up getting insecure with a new serious vulnerability. The whole process of correcting Meltdown and Spectre flaws was confusing, information about the flaw was not new, dated back to 1991, and much of that information was highly complex, which did not make targeting malware an easy task or reach of any “hacker”. But at the same time, fixing the problem has become a headache. An analysis by a security expert has now revealed a new serious vulnerability in Windows 7, the result of the update that was released to fix the issues.
What Ulf Frisk discovered (and revealed) was that Windows 7 and Windows Server 2008 R2 which allowed normal processes to now have full (write and read) access to physical memory. This means that with these new permissions it becomes possible to exploit the system and gain administrator privileges on vulnerable machines.
— Ulf Frisk (@UlfFrisk) March 28, 2019 The failure was introduced in January, with the security update that was released. As Ulf Frisk has revealed, the latest systems are protected and not vulnerable. It has not been simple to correct this problem, which is still far from being resolved. Users are still vulnerable, and as you can see now even the solutions bring new problems. So, what do you think about this? Simply share all your views and thoughts in the comment section below.
Δ